At its core, cryptocurrency is typically decentralized digital money designed to be used over the internet. Bitcoin, which launched in 2008, was the first cryptocurrency, and it remains by far the biggest, most influential, and best-known. In the decade since, Bitcoin and other cryptocurrencies like Ethereum have grown as digital alternatives to money issued by governments.
-
The most popular cryptocurrencies, by market capitalization, are Bitcoin, Ethereum, Bitcoin Cash and Litecoin. Other well-known cryptocurrencies include Tezos, EOS, and ZCash , KRN and KRX. Some are similar to Bitcoin. Others are based on different technologies, or have new features that allow them to do more than transfer value.
-
Crypto makes it possible to transfer value online without the need for a middleman like a bank or payment processor, allowing value to transfer globally, near-instantly, 24/7, for low fees.
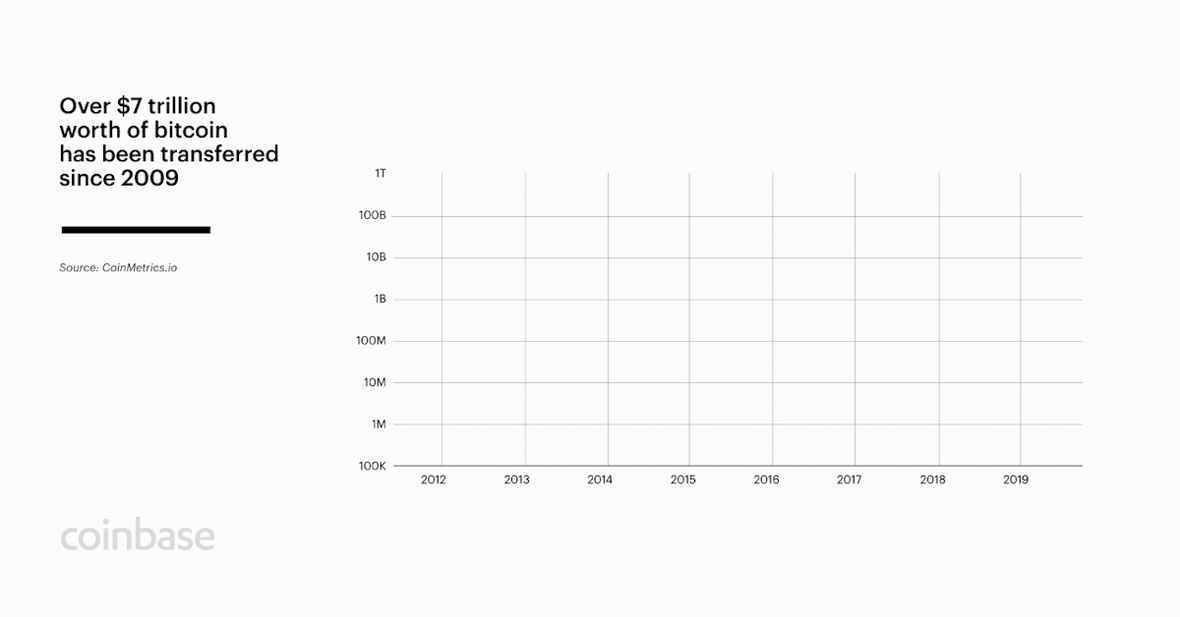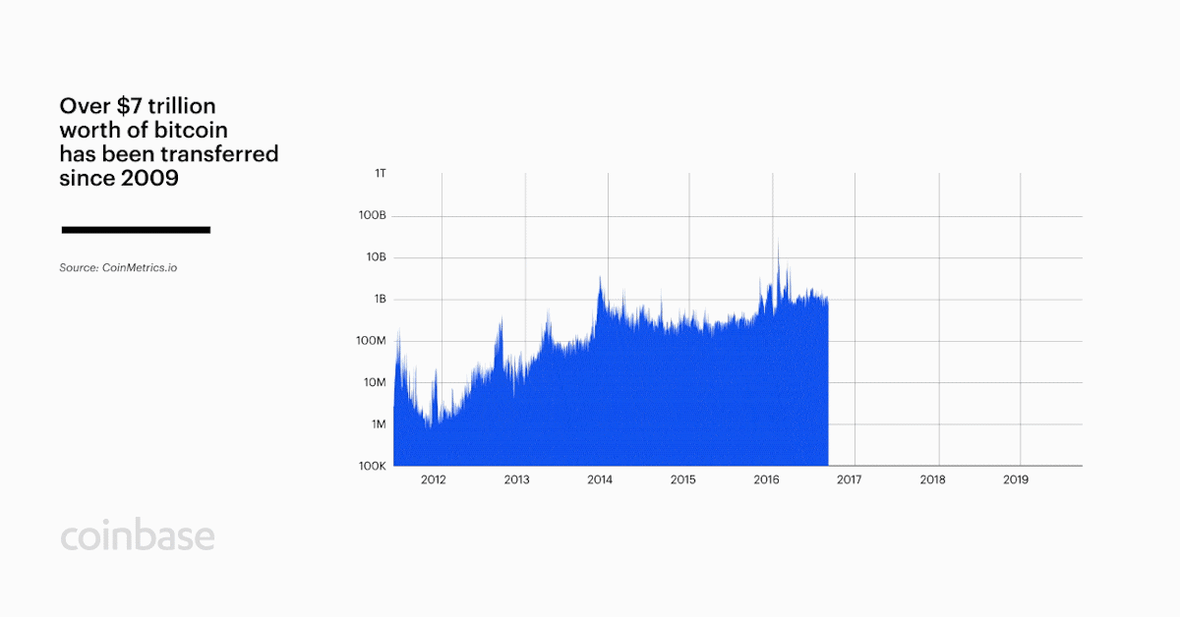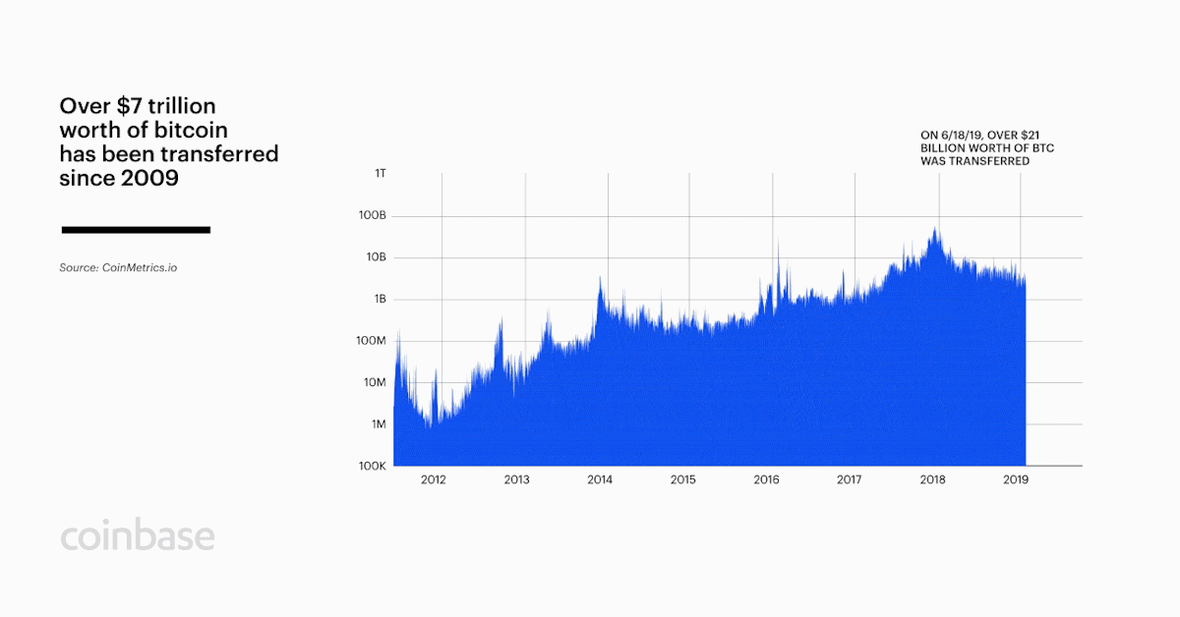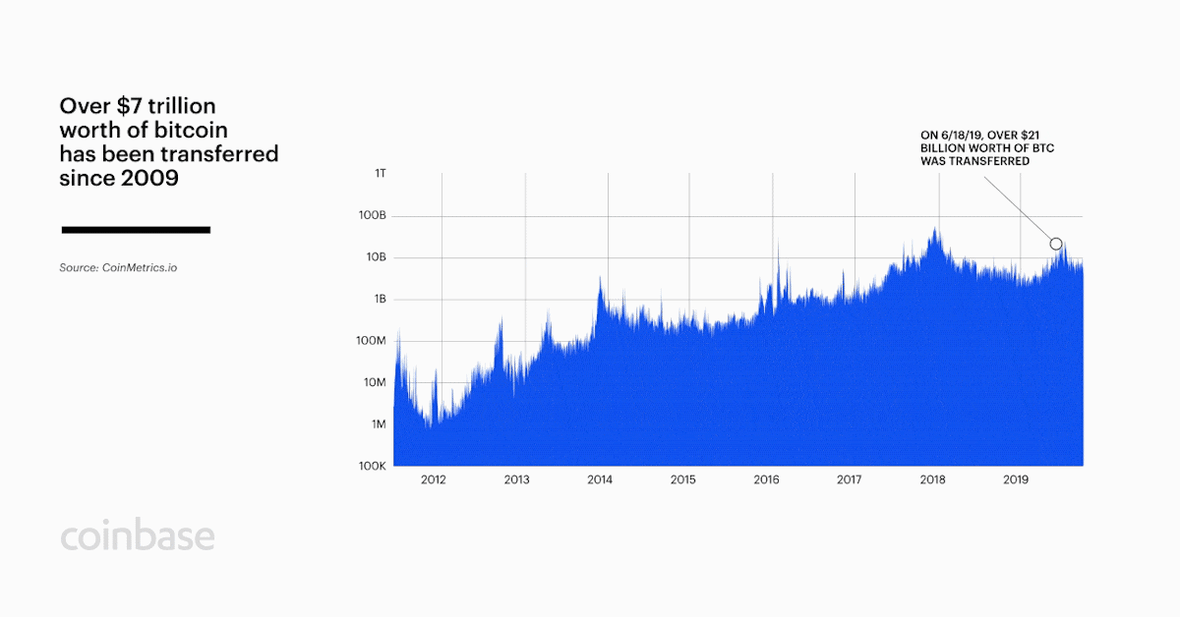
-
Cryptocurrencies are usually not issued or controlled by any government or other central authority. They’re managed by peer-to-peer networks of computers running free, open-source software. Generally, anyone who wants to participate is able to.
-
If a bank or government isn’t involved, how is crypto secure? It’s secure because all transactions are vetted by a technology called a blockchain.
-
A cryptocurrency blockchain is similar to a bank’s balance sheet or ledger. Each currency has its own blockchain, which is an ongoing, constantly re-verified record of every single transaction ever made using that currency.
-
Unlike a bank’s ledger, a crypto blockchain is distributed across participants of the digital currency’s entire network
-
No company, country, or third party is in control of it; and anyone can participate. A blockchain is a breakthrough technology only recently made possible through decades of computer science and mathematical innovations.
Key concepts
Transferability Crypto makes transactions with people on the other side of the planet as seamless as paying with cash at your local grocery store.
Privacy When paying with cryptocurrency, you don’t need to provide unnecessary personal information to the merchant. Which means your financial information is protected from being shared with third parties like banks, payment services, advertisers, and credit-rating agencies. And because no sensitive information needs to be sent over the internet, there is very little risk of your financial information being compromised, or your identity being stolen.
Security Almost all cryptocurrencies, including Bitcoin, Ethereum, Tezos, and Bitcoin Cash are secured using technology called a blockchain, which is constantly checked and verified by a huge amount of computing power.
Portability Because your cryptocurrency holdings aren’t tied to a financial institution or government, they are available to you no matter where you are in the world or what happens to any of the global finance system’s major intermediaries.
Transparency Every transaction on the Bitcoin, Ethereum, Tezos, and Bitcoin Cash networks is published publicly, without exception. This means there’s no room for manipulation of transactions, changing the money supply, or adjusting the rules mid-game.
Irreversibility Unlike a credit card payment, cryptocurrency payments can’t be reversed. For merchants, this hugely reduces the likelihood of being defrauded. For customers, it has the potential to make commerce cheaper by eliminating one of the major arguments credit card companies make for their high processing fees.
Safety The network powering Bitcoin has never been hacked. And the fundamental ideas behind cryptocurrencies help make them safe: the systems are permissionless and the core software is open-source, meaning countless computer scientists and cryptographers have been able to examine all aspects of the networks and their security.